reCAPTCHA
As of LiteSpeed Web ADC v2.4, reCAPTCHA is available as a method of defense against DDoS attack.
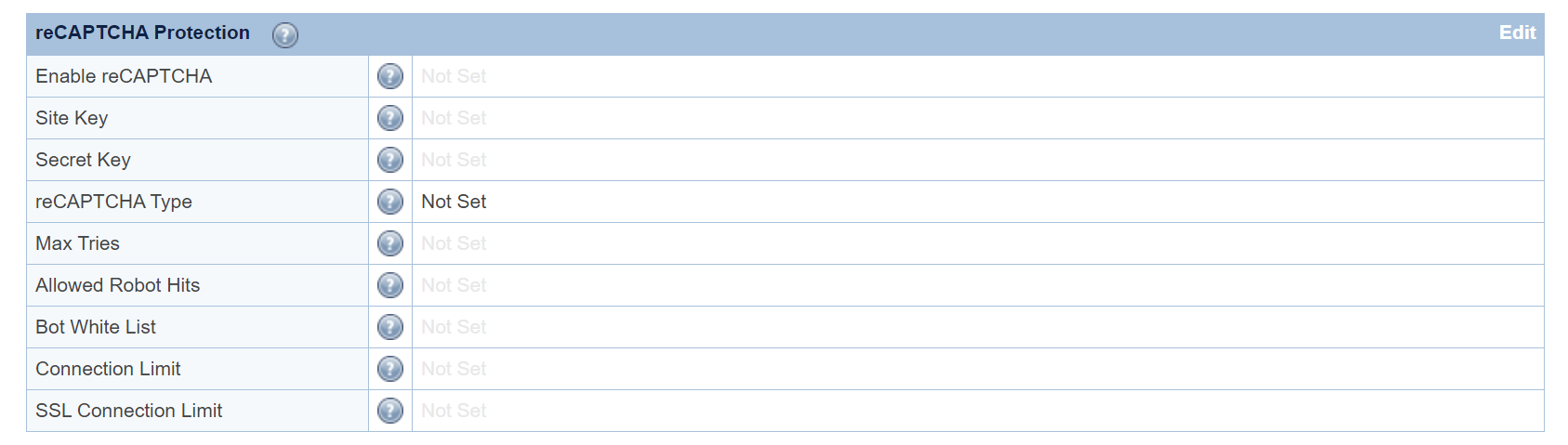
Enable Globally at the Server Level
Access the WebAdmin console via https://YOUR_SERVER_IP:7090
Navigate to Configuration → Server → Security → reCAPTCHA Protection
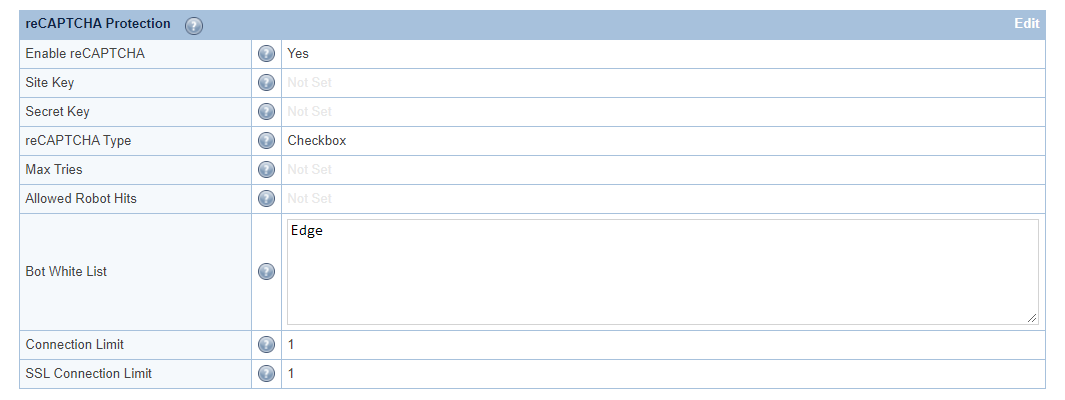
Set Enable reCAPTCHA to Yes. This is the master switch.
It will enable the reCAPTCHA feature for the entire Web ADC.
It may be overridden at the virtual host level.
For other options, hover over the ? symbol to view detailed information about that option.
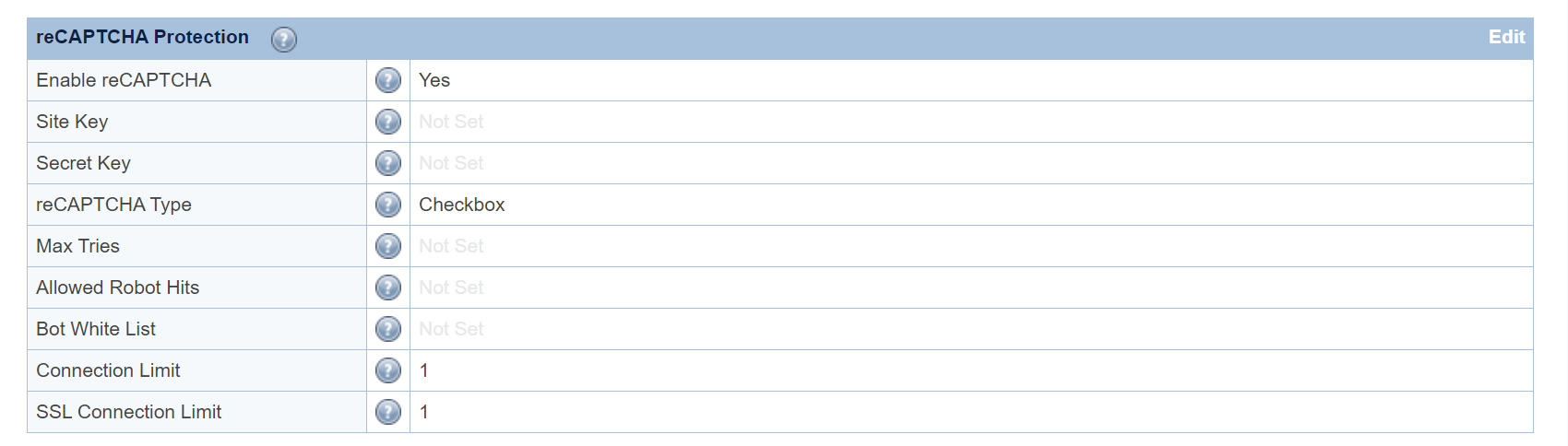
For demonstration purposes, we will set Connection Limit and SSL Connection Limit to 1,
and reCAPTCHA Type to Checkbox. You may adjust these values according to your needs.
Save and restart the Web ADC. This conneciton limit setting will be inherited by all
virtual hosts unless overridden at the virtual host level.
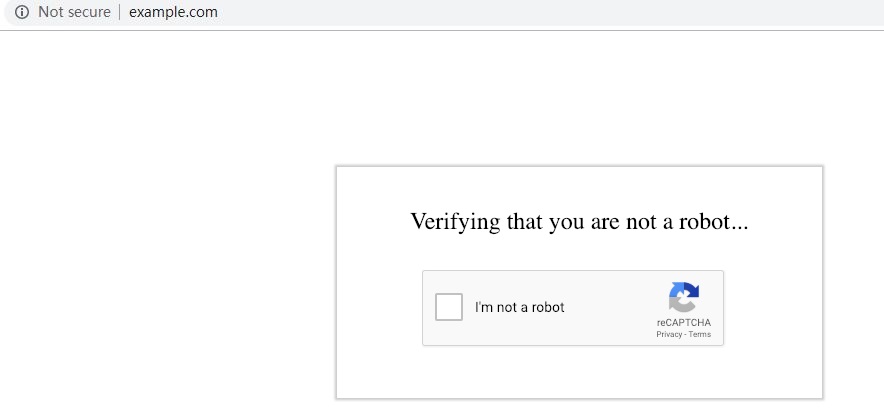
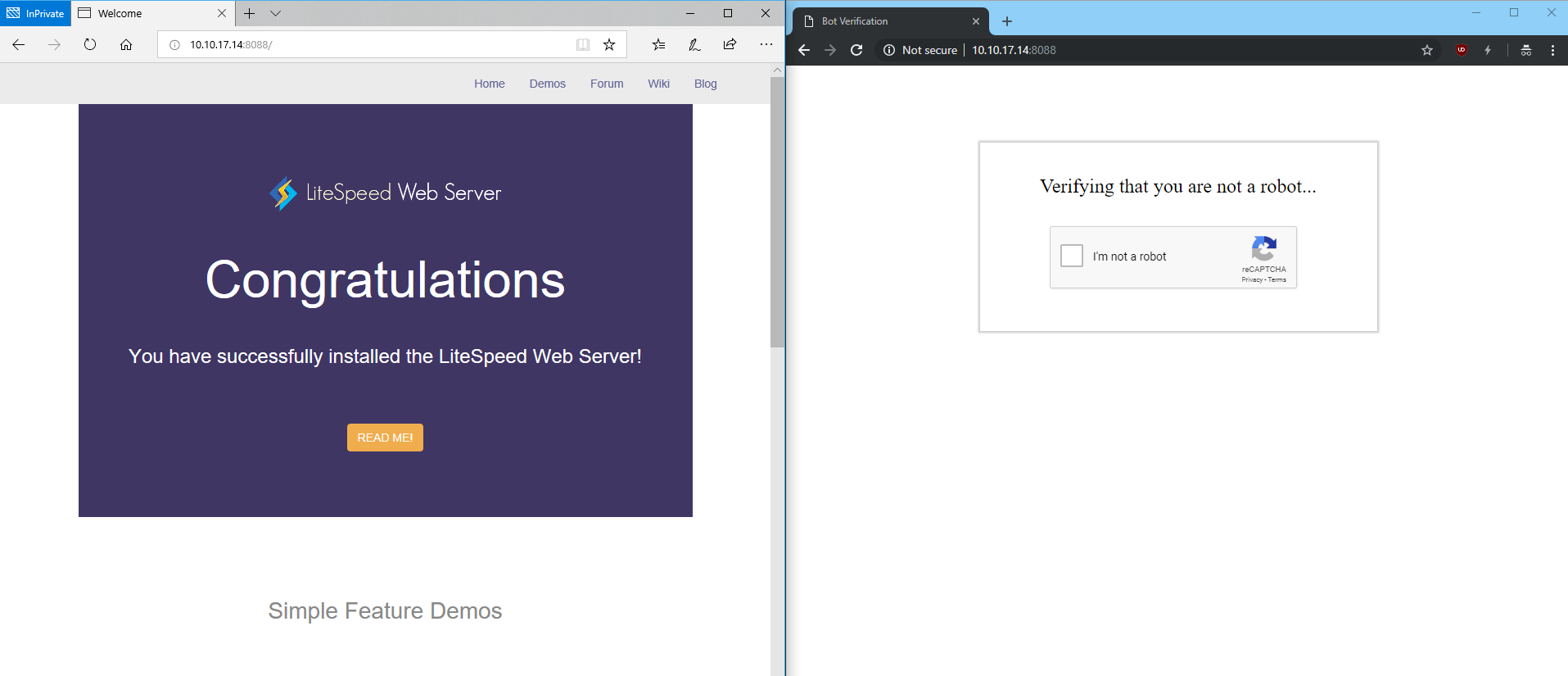
When a visitor accesses the website, they will need to go though reCAPTCHA validation. This validation protects the server against HTTP Flood and other DDoS attacks.
After passing the reCAPTCHA validation, the visitor is temporarily whitelisted as long as they continue to browse the site. This makes for a better user experience. Once the visitor has been inactive for more than 20 minutes, reCAPTCHA is once again enabled for that visitor's next request.
You can also enable reCAPTCHA on an individual virtual host that is under attack, while leaving other websites disabled.
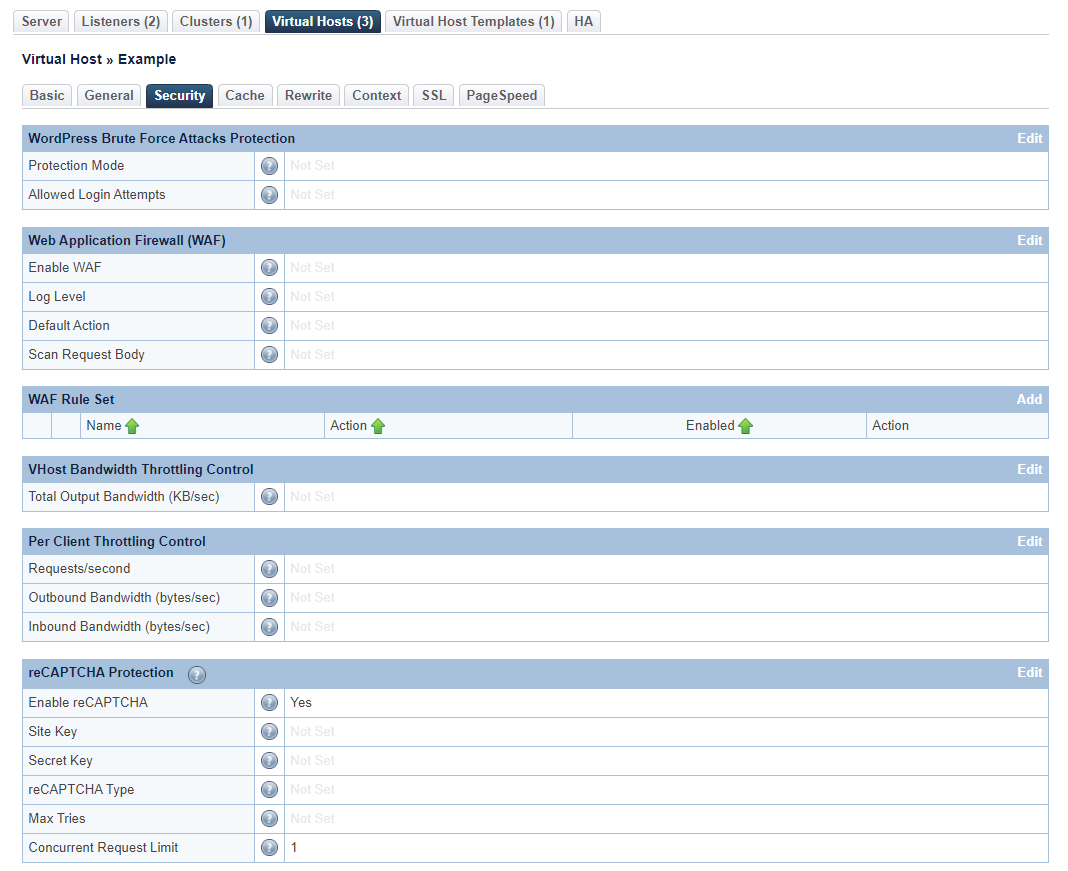
Override/Disable at the Virtual Host Level
Assuming you have enabled reCAPTCHA at the server level globally, you can override the settings at a virtual host level.
Use the Web ADC WebAdmin console to override reCAPTCHA for the VHost.
Navigate to Configuration → Virtual Hosts → Security → reCAPTCHA Protection
Advanced Configuration: Define reCAPTCHA Actions through Rewrite Rules.
If you want to further define the reCAPTCHA action as deny or drop, you can use
one of the following rewrite rule directives:
[E=verifycaptcha] or [E=verifycaptcha: ACTION]
[E=verifycaptcha] will always redirect to reCAPTCHA until verified.
ACTION can be deny to return a 403 or drop to drop the connection when
Max Tries is reached. Until Max Tries is reached, the client will be redirected to reCAPTCHA.
For example:
RewriteCond SOME-CONDITIONAL-CHECK RewriteRule .* - [E=verifycaptcha]
(SOME-CONDITIONAL-CHECK would be a suspicious UA, IP address, etc.)
NOTE: In most cases, rewrite rules will override the default server behavior. However, in cases where trigger sensitivity is high, visitors may be sent directly to reCAPTCHA before the rewrite rules can even be processed.
Customize the Good Bots List
Google bots are considered good bots because they help index your site. However, they cannot do their job properly without receiving the correct page. The Bot Whitelist configuration may be used to specify bots that you may need for your site.
Here, we have configured Edge in the Bot Whitelist text area.
Bot Whitelist is a contains match (case sensitive), but regex may be used as well.
After restarting, browsers containing Edge in the user-agent header will bypass reCAPTCHA:
The Allowed Bot Hits configuration may be used to limit how many times a good bot (including Googlebot) is allowed to hit a URL before it is redirected to reCAPTCHA as well. This may be useful to prevent bad actors from bypassing reCAPTCHA using a custom user agent.
Customize the reCAPTCHA Page
The default reCAPTCHA page is generic. If you would like to customize the page,
you may do so by creating a file at $SERVER_ROOT/lsrecaptcha/_recaptcha_custom.shtml.
There are two script tags that are required and it is strongly recommended to
avoid changing the form and the recaptchadiv unless you know what you are doing.
There are three echos within the page itself. Those are used by the web server
to customize the reCAPTCHA type and keys and specify any query string used.
Beyond those required attributes, everything else is customizable.
As noted before, please ensure that you have backups of the default page and
your customized page. Note that the .shtml extension is required in order to
use the LSWS configured type and keys.
Apply Your Own Site Key
You can apply your own reCAPTCHA key and adjust the configuration as you like from the Google developer reCAPTCHA page. Client verification is completely determined by Google's reCAPTCHA service. The invisible type may display a difficult puzzle.
For server wide protection that needs to cover a lot of domains, make sure
Verify the origin of reCAPTCHA solutions is unchecked. Otherwise, you may
need to apply a key for each domain. Please refer to
the Google doc.
Troubleshooting
reCAPTCHA Returning 403 and Dropping Connection
If reCAPTCHA fails a few times, it will return a 403 error and then drop the
connection from that IP. It works this way in order to block attacks.
If the invisible reCAPTCHA keeps auto-refreshing and then fails,
just change the type to one-click.